Special feature of 1905 film network The original may be late, but the shanzhai is not absent.
Since the opening of "Lotus Root Cake" CP, (hereinafter referred to as "Nezha") has swept all box office records of animated films in the domestic market. This treasure boy is now among the top ten clubs in the box office of domestic film history with a value of 2.6 billion.
Going out of the circle is like a double-edged sword, and the troubles of the teenager "Nezha" follow. In the pre-sale and crowdfunding stage of authorized derivatives, the surrounding areas of the cottage have already landed on the market.
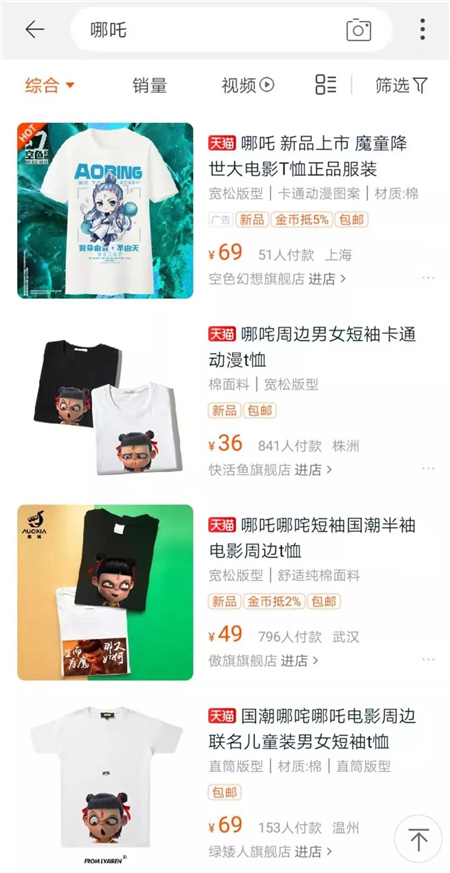
Taobao searches for "Nezha", and T-shirts are flooding.
In this regard, Light Film recently answered questions from investors on the interactive platform, saying that the company has a high proportion of investment in the film Ne Zha, and the company enjoys the copyright of the film and the exclusive right to develop film derivatives and attract investment. The company attaches great importance to copyright protection, has fully implemented the management of copyright assets, and used legal and technical means to crack down on infringement and piracy and safeguard the rights and interests of copyright assets.

Film Light Film released a copyright statement letter.
At this time, in a garment printing factory somewhere in Zhejiang, a batch of T-shirts suspected of containing Nezha’s head without authorization have begun to produce "big goods" (in jargon, it means to start mass production).

T-shirts with Nezha’s head have been mass-produced
During the reporter’s investigation, it was found that such garment and mobile phone case processing factories would not screen whether the entrusted producers owned the copyright of the pictures. Sometimes, in order to make a deal, they will take the initiative to help customers find pictures.
The troubles of the teenager "Nezha"
At first, the people in Chentangguan were biased against Nezha, and so many people thought that the box office of animated films had a fixed ceiling. After entering the top ten box office of domestic film history, secular prejudice began to be broken by reality. From studying medicine and crossing the border by self-study to animation production industry, director jiaozi’s career experience is also a process of breaking stereotypes.

Ne Zha director jiaozi.
"Unless you have a box office, you can prove that others like your work, and you can move the surrounding area. You can’t cross the box office and say the surrounding area." In an exclusive interview with 1905 Film Network, director jiaozi defined the relationship between works and peripheral derivatives.
Six months ago, the birth process of derivatives directed by Frant Gwo was the best proof.

There are many kinds of derivatives in The Wandering Earth.
Now that Nezha is on fire, the production of peripheral derivatives has started.
In the process of collecting relevant information, Xiao Dianjun found that two companies were approved by the film official micro-seal, a Taobao shop named "Miaowu Shop" and a company named "Guagua Production". The former is in pre-sale and the latter is crowdfunding.

Taobao shop "Miaowu Shop" is being pre-sold.
"The current confirmation of cooperation is like this." Zheng Hongwei, a staff member of Light Media, acknowledged this. At the same time, he also said that for the sale of unauthorized products, the company has a special copyright owner and is working on this matter.
According to public data, the sales volume of pre-sale peripheral T-shirts in August has exceeded 8,500, and the amount of crowdfunding derivatives has reached 1,585,500, far exceeding the original target amount of 30,000. Outside the box office, fans use real money to express their love for "Ouba".
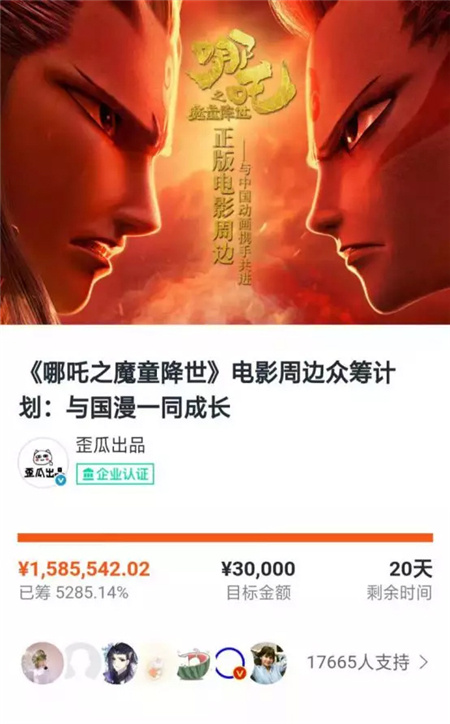
The crowdfunding amount has far exceeded the target.
At the same time, the spot products around the cottage have been released.
A clothing printing factory said that as long as the pattern and clothing size are selected, mass production can be realized within one day, but only if the production quantity is at least 200 sets. Another manufacturer engaged in mobile phone case processing said that it can help find relevant pictures from the Internet. In this process, the two never asked about the copyright of pictures.
"Nezha should be a film and television work, which is protected by the Copyright Law. If the copyright owner takes Nezha’s pattern design to apply for a trademark, the pattern will also be protected by the Trademark Law." Li Lei, who graduated from a university of political science and law, said so.
In her opinion,Pirated peripheral developers who produce and sell unauthorized products violate the Copyright Law and infringe the copyright owner’s right of reproduction and distribution, should stop the infringement and compensate the copyright owner for the losses.
The creator may spend many months trying to pirate a picture.
It is understood that there are 100 versions of Nezha Design, which are jointly participated by many outstanding designers. It took more than a year to finalize the current version. The damage of unauthorized surroundings to a film and television IP goes far beyond the economic scope.

One of the manuscripts of Nezha’s image design exposed by the film
Who moved the "cheese" in the genuine derivatives market?
Nezha, a teenager, had the same troubles as Hu Ba.
As the ticket winner in the summer of 2015 and even the whole year, it became the first domestic film with a box office of over 2 billion. As an important character in the film, the image of "Hu Ba" is deeply loved by the audience, with high popularity and market value. At that time, unauthorized "Hu Ba" derivatives flooded the market.

Around the "Hu Ba" cottage exposed by netizens.
Why is this phenomenon repeated?The low cost of violating the law and the high cost of safeguarding rights are two recognized reasons in the industry.
It is generally not illegal for consumers who know that it is pirated and still buy it, but only use and appreciate it themselves. However, if it is disseminated, developed and used for commercial purposes, it will be infringing. Sun Yueyue, who worked as a legal adviser in a law firm in Kunshan, said so.
For pirated manufacturers, peripheral derivatives, such as T-shirts, mobile phone cases and charging treasures, have low technical requirements and low cost of dissemination and reproduction. Even if it is punished, it is usually destroyed or fined.
"At present, the production of authorized derivatives in China is basically based on OEM, that is, the name or photo pattern of the film is engraved on the original model of the manufacturer, such as lettering on charging treasure and T-shirt. Basically, it will not be specially designed for derivatives, but there are also small objects such as USB flash drives that will be combined with movie elements and designed to be more fun. " The media director of a film marketing company said that this is also the reason why there are thousands of people in the form of domestic derivatives.

Nezha authorized T-shirt printing exhibition
The high cost of safeguarding rights is because it is difficult for the obligee to find evidence of infringement of others, for example, the sales channels are complicated, or many sales are completed through the Internet, so it is difficult to obtain evidence.
In addition, in people’s traditional impression, price has a great influence on consumers’ decision whether to buy genuine derivatives. In the survey of Xiao Dianjun, it was found that the proportion of price factors was lower among the people who mainly bought after 1990.
When most consumers buy derivatives such as movies, they first pay attention to whether the products are officially authorized, and those authorized are more collectible. In terms of product quality, the official production is usually more sophisticated, with better texture and higher degree of reduction.

Authorized water bottle
"If you can’t afford genuine products, you won’t buy pirated products. Some pirated products are really inferior." Xu Ziqi (pseudonym), a 15-year-old middle school student, has a firm tone. Although his spending power is limited, he will occasionally buy some genuine animation peripheral products.
Some netizens suggested that the products around Guoman and movies can be offered at different price points to choose from. "For example, according to its complexity and rarity, hand-made shops in Japan have different pricing, so fans can also choose suitable collectibles according to their own economic situation."
In addition, the creativity of derivatives has also become one of the important factors for consumers to buy products. This is consistent with the personality portrait of the whole crowd who pursued individuality and dared to express themselves after 1990.
The normal production of domestic film derivatives: first out of the circle, then production
From "monster hunt 1" to "The Wandering Earth" and "Nezha", domestic film derivatives are usually made after the film is released.
Jiang Zhiqiang, the first producer of monster hunt, said in an interview with the media that "I didn’t pay attention to derivatives before, but now I regret it, and I will definitely pay attention to this matter in the future." However, similar incidents are still being staged.

Monster hunt authorized the doll.
The fundamental reason lies in the instability of the quality of film and television works and the unpredictability of market reaction. According to the conventional process, the development of derivatives has been started before the film is completed, even at the stage of script development. The sales performance of most derivatives is directly proportional to the popularity of the film.
Before the film was released, there were many uncertainties in the market. If the peripheral products are developed and distributed at this time, the potential business risks are huge. In order to avoid risks to the greatest extent, most copyright owners choose to say it after screening.
Fu Xiaoran, the general manager of Alibaba Fish Market, a domestic derivative head production company, believes that it is ideal and perfect to enter the development stage of derivatives half a year before the film is released, because all good derivative products need a development cycle of about half a year, so that when they are in stock, they can catch up with the popularity of film release, jointly promote brands and promote sales.

Ne Zha derivative service presentation
However, she also admitted that due to the high uncertainty of the film, many popular films after the release did not have derivative development in the early stage, which led to temporary follow-up authorization, which was unfavorable to both the merchants and the film copyright parties.
"At that time, the surrounding area was very popular, and the reservation volume was very high, but the production cycle was long and the customer waited for a long time. There seems to be no continuous production of peripheral products now. I think this should be used as a long-term marketing, not just during the movie fire. " Chen Tiantian (a pseudonym), a graduate student studying at China Communication University, recalled.

"The Return of the Great Sage" is officially done.
As a fast-moving consumer product, movies lack lasting influence compared with comics that can be serialized for decades at the longest. The surroundings built on the works naturally have the worry of being "out of breath". As the popularity of the film fades, it is reasonable to update the product in the later stage.
Relatively speaking, animated films, costume fantasy and sci-fi works have more potential in derivative development. "However, the premise of these is that movies are explosions, and it is more difficult for real-life urban dramas." Fu Xiaoran stressed.
After monster hunt and The Return of the Great Sage, Big Fish Begonia, Begonia and other films have begun to lay out derivatives business in advance. According to the Securities Daily, before the release of "Catch the Demon 2" in 2018, the legally authorized Aojieer Hu Ba plush doll sold nearly 200,000 pieces on Taobao platform, with a sales volume of nearly 4 million yuan.

Aojieer Hu Ba plush doll
On the whole, the content quality of the film itself is the best spokesperson for related derivatives. First out of the circle, then production, is the mainstream choice for the production of mainland film derivatives.
Waist derivatives production companies are scarce.
"I don’t know."
In the process of film derivatives investigation, faced with Xiao Dianjun’s request to recommend several contacts of domestic regular derivatives production companies, many friends answered highly similar questions. Waist derivatives production companies are scarce or the industry is normal.
After many twists and turns, I finally contacted Wang Yangyang, co-founder of Chuangfeng Media. According to its introduction, the company was established in 2014, mainly providing a complete set of derivative solutions for the entertainment industry. The company has served more than 100 cinema film projects.
Baidu Encyclopedia Entry of Chuangfeng Media
At the beginning, because of the feelings and expectations of the film derivatives industry, the company is now expanding its short video marketing business. "Derivatives are oriented to the C-end development direction, development cycle and marketing cooperation, which leads to the market not being fully opened; Because of the big market environment, the customized promotional products have changed a lot in the promotional budget. " After doing film derivatives for many years, Wang Yangyang is so impressed.
As we all know, the well-known derivatives production companies in the industry include Ali Fish and Entertainment Cat.
The former once launched movie derivatives such as The Wandering Earth Planetary Engine Model and Carrier Vehicle Model, which were jointly created by Saffan Science Fiction Space and China Film Marketing, on its own crowdfunding platform, while the latter was independently responsible for the derivative development of The Return of the Great Sage.

The Wandering Earth planetary engine model launched by Ali Entertainment on crowdfunding platform.
In addition, if you don’t have a deep understanding of this industry, it is difficult to name other companies.
After the accumulation of time and skills, in 2019, domestic science fiction films and animated films reached unprecedented peaks respectively. Although there are some problems in the film and animation derivatives industry with huge potential market, its future development is full of imagination.
(Intern Nan Zhou also contributed to this article)