Reminder | New scam! Do you know the mobile phone extension? Someone lost 50 thousand overnight
CCTV News:Pretending to be an acquaintance to borrow money, pretending to be a public security bureau, a procuratorate or a court officer to investigate a case, and hiding a Trojan link &hellip in short messages and QR codes; … These tricks must have made everyone immune, but do you know? Some telecommunications services that you have never heard of have also begun to become new traps set by scammers!
The mobile phone was locked and more than 50,000 yuan was stolen.
When he woke up, Mr. He in Shenzhen found that his mobile phone was locked. At the same time, a shopping platform account was stolen by strangers. Criminals used white bars to spend and apply for loans, and robbed more than 50,000 yuan overnight.
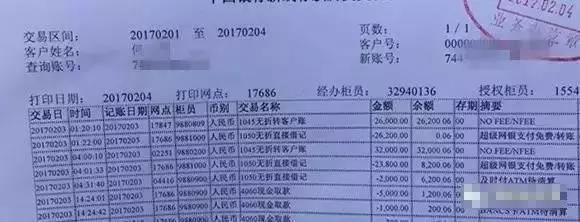
Later, Mr. He discovered that his mobile phone had been taken over by a strange number. The short message from the operator shows that this is a business to add a secondary number, and Mr. He’s mobile phone number was added as a secondary number by criminals. When the secondary phone is turned off, all short messages will be received by the primary phone, and criminals will receive Mr. He’s short message verification code during this period, and then commit crimes.
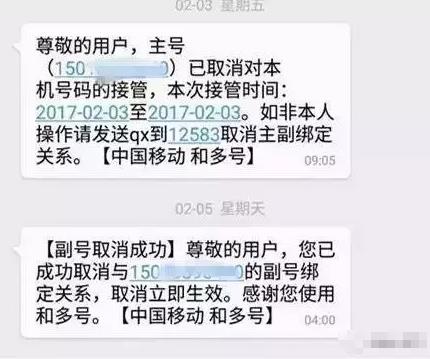
"Subnumber" ≠ "kinship number"
Without an ID card, a bank card or even a real name, the money is gone. What the hell is a minor number?
Many people think of "family number" at first, but "deputy number" and "family number" are not the same thing.
Family number usually refers to the phone bill package opened by different owners and different numbers in order to make calls between them cheaper, and the secondary number is the "one card with many numbers" service provided by operators. On the basis of not changing mobile phones and SIM cards, users can add up to three real mobile phones as secondary numbers. The main and auxiliary numbers can stand by at the same time, and you can freely choose any number to dial, answer the phone and send and receive short messages as needed.
Don’t reply to text messages too casually.
Then, how did Mr. He’s mobile phone number become the "secondary number" of criminals?
Reduction of criminal modus operandi
Step 1: Buy materials.Criminals buy leaked names, bank card numbers, ID numbers and reserved mobile phone numbers online, commonly known as "four big pieces".
Step 2: Fishing.Criminals apply to the users who have mastered the bank card information, initiate the business application of binding the sub-number, and find the target of the crime by casting a net widely. Once you reply by mistake, you are hooked.
Step 3: Forced shutdown.Because the main number can only take over the SMS when the secondary number is turned off, criminals usually use two means at this time. One is to use SMS bombing to force the target to turn off the mobile phone, and the other is to use the mobile phone cloud service to remotely operate the mobile phone.
Step 4: White Wolf with Empty Gloves.Using the SMS verification code received by the main number, criminals ransacked the online shopping account bound to the mobile phone number.
Patterns are stacked, and it is impossible to prevent them! For this kind of fraud, after receiving all kinds of SMS notifications, you must read the content of the SMS clearly and do not reply at will.
"SMS custody" business is also not very secure.
After the SMS storage service is opened, you can save your mobile phone messages on the server of the operator. Now, many mobile phone manufacturers’ cloud services are doing the same thing. However, this is a hidden danger function.
Case review
One morning, Miss Ding saw two short messages from banks and mobile phone operators on her mobile phone, which were sent at 3:43 am and 4:12 am respectively. As soon as the account is checked, the balance of more than 100,000 yuan will be zero overnight! Not only that, Miss Ding also suffered a credit card theft and was "applied" for a bank universal loan of 70,000 yuan.
How on earth did all this happen?
Reduction of criminal modus operandi
Step 1: Hit the database to get all kinds of account information.The so-called "library collision" means using software to try a high probability digital sequence. Using this simple and rude method, the user’s network identity, online banking account number, mobile phone business hall and other accounts can be seen at a glance. Insiders said: "The speed of library collision is very fast, at least thousands per minute. If some good equipment is used, the efficiency is higher and the success rate is above 50%."
Step 2: Open SMS storage and SMS interception services to obtain verification code.This is the most critical step. After the opening of this service, the dynamic verification code to ensure the safety of landing has successfully become the bag of criminals.
Step 3: Open the physical SIM card.At this point, criminals can pretend to be victims and apply for 4G card replacement service in the online business hall. For the convenience of the people, some operators can express the card directly to the designated address.
By intercepting short messages and copying SIM cards, fraudsters can "do whatever they want".
As we all know, many important services rely on mobile phone authentication. If you back up the SMS to the server synchronously, it will increase the exposure opportunity. Once the service password of the online business hall is stolen, or the login permission of the cloud service is stolen, it is equivalent to "swimming naked".
The loopholes in the unpopular business are targeted by scammers.

The "Research Report on the Trend of Online Fraud in 2016" released by the anti-fraud reporting platform "Hunting Network Platform" proposes that since 2016, online fraud has mainly shown several obvious characteristics:
Mobile phone cards have become new theft targets;
Jump to the phishing website by using short URL and weiyun sharing link;
Well-known recruitment websites and voice platforms for open recruitment;
A phishing website that is difficult to distinguish between true and false;
The implementation of precision fraud;
Fraud professionalism is getting higher and higher;
Using loopholes in new business and unpopular business to commit fraud;
Use cloud disk and synchronization software to steal information.
Among them, the loopholes in mobile phone cards and unpopular business are mentioned.
Security experts suggest that we should develop good online habits, don’t click unfamiliar links, don’t fill in our personal information in the website interface with unknown security, and regularly modify the password of social accounts to avoid information such as mobile phone contact information being leaked; Improve safety awareness, develop good habits of using mobile phones, and avoid being infected by mobile phone viruses.